Security Gateway Appliance
Today all organizations are threatened more intensely and effectively. And the increasing reliance on computer networks can compromise the continuity of your business or organization. The backlogs of anti-virus protection were long overdue, even systems previously known as "secure", are now the target of attacks that result in the loss of information or the compromise of sensitive data, including the hijacking of information.
Sites like Have i been pwned? Keep track of large companies and systems that have been compromised by detecting 1,444,567,928 accounts in 142 global sites. Linkedin's importance sites; Companies such as Adobe; And services like Dropbox. Whose main business is technology have been compromised. And not to mention information committed to governments and institutions around the world.
How safe is your network?
It is a fact, your organization needs protection. The figures are compelling, and the reality about computer security is frankly worrisome. For some years now, we have perceived how thanks to the films and TV, the perception that has about the "hackers" and the vulnerabilities, it seems that it is a science fiction.
With the growing reliance on technology, more and more information circulating around the network, information is certainly very sensitive to organizations such as electronic billing. It is becoming increasingly necessary and indispensable to have mechanisms that protect our information.
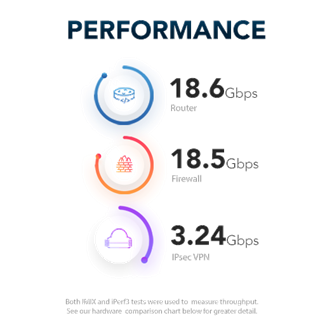
Security Gateway Appliance (SGA), fulfills this purpose. It has features that allow you to protect your networks in an integral way. Provides protection to your communications and your equipment from a single device. In addition, we have different models to protect from small networks, to very complex corporate networks.
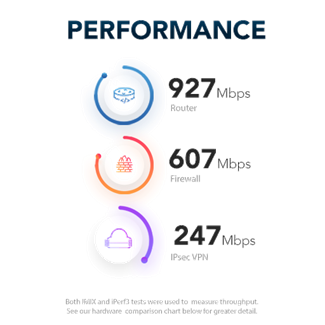
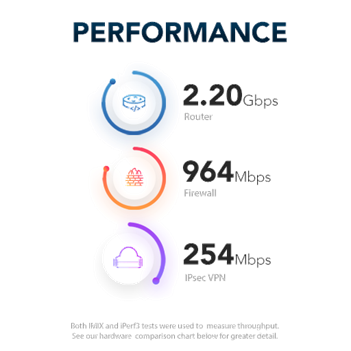
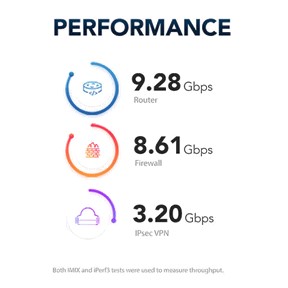
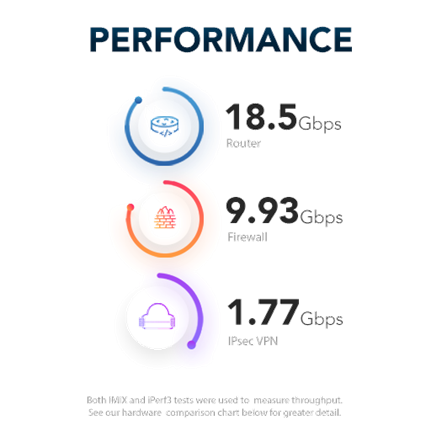
Models