
360º SECURITY IN REAL TIME
fast implementation | No administration overload | AI threath hunting
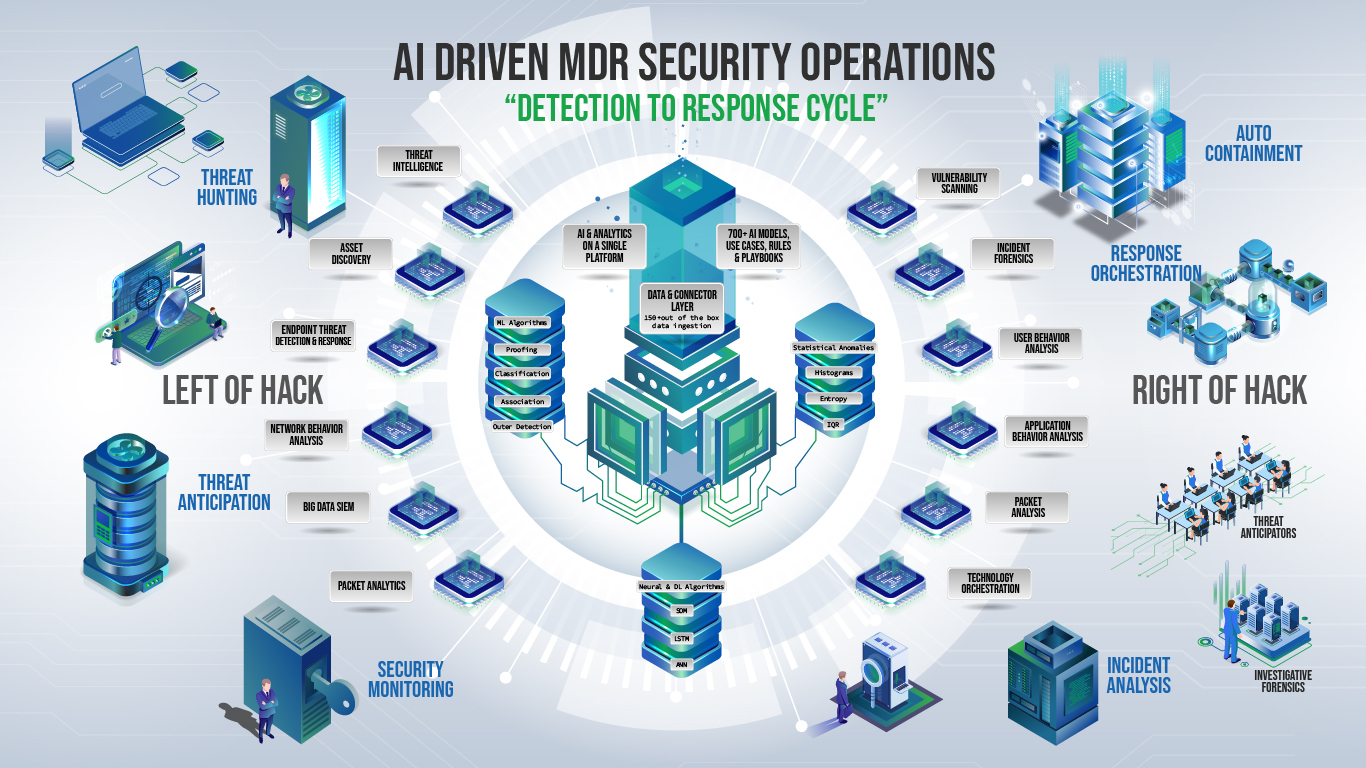
Managed Detection and Response services are designed to enhance an organization's ability to detect and respond to cybersecurity threats. MDR services typically involve continuous monitoring of an organization's network and endpoints for signs of malicious activity.
Key aspects of Managed Detection and Response may include:
- Continuous Monitoring : MDR services involve the ongoing monitoring of an organization's IT environment for potential security incidents.
- Threat Detection: MDR providers use advanced tools and technologies to detect unusual or suspicious activities that could indicate a cybersecurity threat.
- Incident Response: In the event of a security incident, MDR services provide rapid and effective response measures to mitigate the impact and contain the threat.
- Forensic Analysis: MDR providers often conduct in-depth forensic analysis to understand the nature of a security incident, identify the root cause, and prevent similar incidents in the future.
- Security Expertise: MDR services are typically delivered by cybersecurity experts who have the knowledge and skills to interpret security data, analyze threats, and respond effectively to incidents.
MDR is part of the broader landscape of cybersecurity services, and it plays a crucial role in helping organizations proactively defend against and respond to cyber threats.

USER BEHAVIOR ANALYTICS
Network Traffic Flow Analytics

Deep Inspection Analytics Information

Detection & Response Workloads

Integration, Monitoring and Detection

Correlation through Artificial Intelligence (Big Data)
Detection and Response in Computing Equipment

Vulnerability Scanning and Management

Security Configuration Assessment
REGULATORY COMPLIANCE | NIST-800-53 | GDPR | HIPAA | PCI-DSS | MITER & ATT&CK | CIS BENCHMARK
WHAT HAVE WE IMPROVED AND SOLVED?
Models
- Quick and even automatic containment of incidents found with machine learning algorithms.
- Advanced threat analysis using machine learning and the expertise of threat hunters.
- Ability to have containment procedures built and updated for manual or automatic incident response.
- Machine learning capabilities for advanced analysis of network and security data in structured and unstructured formats.
- Network threat hunting uses AI in network sources and enables attack hunting.
- Support multiple configuration parameters for servers/desktops and report misconfigurations.
Deliverables
- Weekly report of user accounts with administrator privileges that had activity in the period.
- Weekly report that shows by day the IP addresses registered with the most hits corresponding to the “Malware beaconing” threat hunting model in the period.
- Daily special protocol report with actions to strengthen prevention measures in the event of a possible cybersecurity incident that could affect the technological infrastructure of the CFE.
- Weekly report with events in the ransomware period detected by the DPI/NTA, Firewalls and MDR Agent solutions.
- Weekly brute force report. Lists the hostnames involved in the Brute force model that were active in the period.

